Is BigCommerce secure? Bigcommerce security tutorial and apps
If you are starting an e-commerce store, you should probably be aware that your online business can be a spot for denial of service attacks, which are also known as cyber-attacks. Those hackers usually aim at personal and commercial data, leading to both losses of data and the brand’s prestige. Therefore, they will severely affect your businesses regardless of their size.
As a result, e-commerce owners have been raising awareness about these problems and also making efforts to increase their security measures. According to a VMWare Carbon Black 2020 Cybersecurity Outlook report, 77% of business owners that were asked had bought new security products in the last year, and 69% had raised the number of security staff.
However, your effort to solve these cyberattack problems is sometimes the same as the game of cat and mouse. When Ecommerce owners update more innovative technologies to their BigCommerce store so that they can stay competitive, those would-be thieves also level up their skills and try a new way, finding the new cavities to start their exploiting plans. Hence, the best solution to these issues is to stay ahead, which means being aware of e-commerce security best practices and the kinds of attacks to be on the lookout for.
What is eCommerce security?
As a response to the increase in the repetition and complication of recent cyberattacks, e-commerce security has been paid more attention. Ecommerce security is known as the measures that are needed to be taken in order to protect your online business and your customers against the threats that cyberattacks can cause.
Before you start, do have a look at the below definition and widely-used phrase:
1. Payment Card Industry Data Security Standard (PCI DSS)
Payment Card Industry Data Security Standard (often called PCI) is a set of security standards formed in 2004 by Visa, MasterCard, Discover Financial Services, JCB International, and American Express that aims to secure credit and debit card transactions against data theft and fraud. PCI is a requirement for any business that processes credit or debit card transactions.
International Organization for Standardization (ISO) is the international standard that experts agree about making a product, managing a process, delivering a service, or supplying materials. You can think of ISO as a formula that describes the best way of doing something as these standards cover a huge range of activities.
One of ISO’s standards is ISO/IEC 27001:2013, which mentions data security. To get an ISO/IEC 27001:2013 certification, your business is required to have an excellent operation system, data security, risk-aversion strategies, and standardized business practices.
2. Personal Data
Any data which can relate to a particular individual is commonly known as personal data. This, most simply, contains names, email addresses, and phone numbers. However, things can become a little more complicated as well. Any data set that is able to classify a person is also referred to as personal data despite the fact that they scrubbed of particular names or numbers.
It is necessary that Personal Data be protected, especially under some data privacy regulations like GDPR.
3. Transport Layer Security (TLS), Secure Sockets Layer (SSL), and HTTPS authentication
Transport Layer Security (TLS) is a popular security protocol that is designed to facilitate privacy and data security for communications over the Internet. TLS helps to encrypt the communication between web applications and servers, such as web browsers loading a website.
Secure Sockets Layer (SSL) is also an encryption-based Internet security protocol that ensures privacy, authentication, and data integrity in Internet communications, and SSL is the predecessor to modern TLS encryption.
The way SSL works is that if you get an SSL certificate for your store website, you will be able to move from HTTP to HTTPS, which lets your shoppers know that your site is safe.
4. Multi-factor authentication (MFA), 2-factor authentication (2FA), or 2-step verification (2SV)
MFA, 2FA, and 2SV are able to replace the others as there are some similarities between them. All three of these methods require you to fill in a username and password. In addition, MFA, 2FA, and 2SV also need at least one further method of identity verification of a user logging into a site.
However, they do have some differences that will be explained below:
- 2-step verification is likely to require web users to fill in a one-time code that can be sent via an email, text message, or phone call.
- 2-factor authentication is a little more sophisticated as this method wants web users to verify their login attempt through another device, for example, opening a particular app on a mobile device while logging in from a personal computer.
- Multi-factor authentication is related to 2-factor authentication, but MFA can refer to the implementation of more than two factors of authentication.
5. A distributed denial-of-service (DDoS)
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
From a high level, a DDoS attack is like an unexpected traffic jam clogging up the highway, preventing regular traffic from arriving at its destination. As a result, it will block your customers out of your store.
6. Malware and ransomware
When would-be thieves plan their attacks at your site, they will install malware or malicious software on your system. Ransomware is a kind of malware that keeps you out of your system or will prevent you from accessing data until you pay a ransom to the attacker.
Below are some signs that may tell you if your system is infected or not:
- When you click on links, they lead you to the wrong page address
- There are some new toolbars or buttons on your browser or new icons that appear on your desktop
- When using your browser, a near-constant barrage of ad show up
- You experience system crashes or slow down
- Your browser freezes again and again and becomes unresponsive
- You experience constant email bouncing
Common security threats your store may face
There are various types of threats that your store may face, and it is extremely difficult to mention all of them in just one article. Therefore, I would like to list some common security threats which are on the top of the threat list that you should know about for strong e-commerce security.
1. Phishing
Phishing is a cybercrime in which a target or targets are contacted by email, telephone, or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, passwords, account numbers, social security numbers, banking and credit card details, and passwords… BigCommerce Note: BigCommerce will never send you an email with a link to update your store or your login credentials under any circumstances. Hence, if any email, phone call, or text from “BigCommerce” requires you to provide personal information, please contact customer support directly for validation.
2. Malware and ransomware
As mentioned above, malware or ransomware - a type of malware - is used by attackers to lock you out of all your important data and systems. And for sure, if this attack happens, it will hugely affect your online business. Therefore, you spend your time backing up data from your site regularly to protect your business from this devastating threat. One more necessary thing is that you must not click on suspicious links or download unknown software on your device.
3. SQL injection
Your e-commerce site may be in danger if you do not store data in a SQL database securely. You should validate rightly to keep your site from a malicious query that is injected into a packaged payload. This payload is able to give the attacker access to view and even maneuver your information, which is stored in the database.
4. Cross-site scripting (XSS)
Cross-site scripting is a type of attack that will insert a piece of malicious code (commonly JavaScript) into a webpage. Nonetheless, this code will not affect the site itself like other kinds of attacks, it would impact the users of that page. These users can be your customers and this cross-site scripting will lead them to malware, phishing attempts, and more.
5. E-skimming
E-skimming is a method used for stealing credit card information and personal data from payment cards as well. When it comes to E-skimming, cybercriminals will introduce skimming code on e-commerce payment card processing web pages to capture credit card and personally identifiable information and send the stolen data to a domain under their control. Attackers get access to your e-commerce site through a successful phishing attempt, brute force attack, XSS, or third-party compromise, after that, they will capture in real-time the payment details that your customers fill on the checkout page.
Is BigCommerce secure?
“Is BigCommerce secure?” is a question that is frequently asked by almost all BigCommerce business owners. In order to answer this question, I would like to divide it into two separate parts: BigCommerce customer security and BigCommerce account security.
BigCommerce customer security
BigCommerce provides customers with the most up-to-date security practices. It will make sure that customers will experience a secure shopping process.
When organizations deal with credit card and debit card information, they must exactly follow the information security standard called Payment Card Industry Data Security Standard (PCI DSS). This security standard was created by the Payment Card Industry Security Standards Council with the purpose of protecting card owner’s data used for online payments.
BigCommerce meets all six categories of PCI standards, which certify BigCommerce Level 1 PCI DSS compliantly:
- manage network securely
- manage a Vulnerability management program
- networks are regularly monitored and tested
- implement strong access control measures
- keep up an information security policy
- this compliance is applied to all BigCommerce online stores
BigCommerce account security
The Shared Responsibility Model provides the best way to approach data security for a cloud-based tool like BigCommerce:
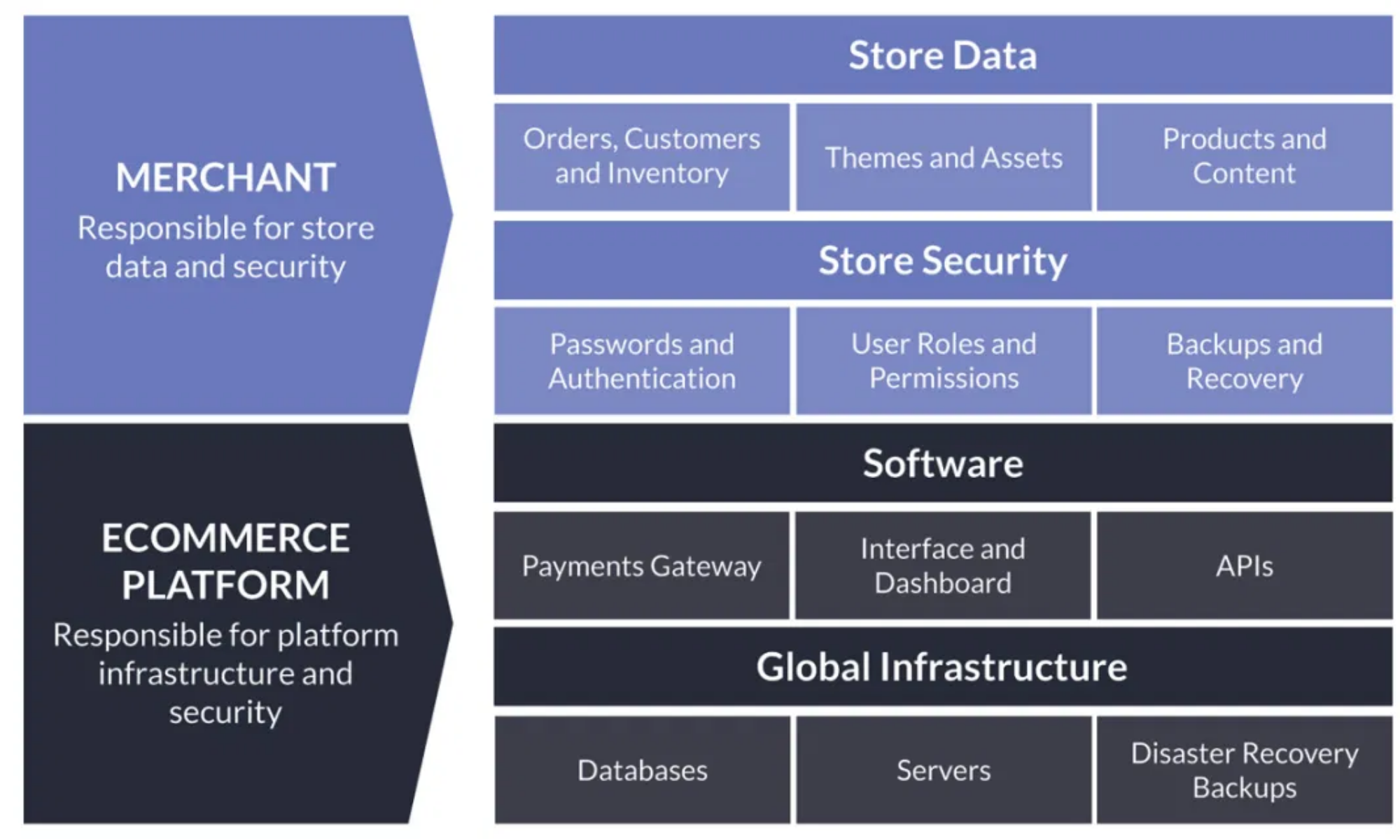
The Shared Responsibility Model makes it clear that protecting your BigCommerce store’s data from any threats is a shared responsibility between BigCommerce and you, the account owner. This model explains that the software, foundation, and disaster recovery of the entire platform will be taken care of by BigCommerce. Users are responsible for password security, permissions are given to users and third-party apps, and also backups of the data they put into their accounts.
Moreover, extensive precautions will be taken by web app developers to make sure their infrastructure will not fail, and about 99.98% of the service will be available. These app providers always have a whole team that is dedicated to the platform’s availability. This makes BigCommerce become a very profitable service for users.
For example, when there is an unlikely circumstance that one of BigCommerce’s data centers is damaged, the latest backup of the entire platform will be recovered immediately by the security team. The duration of this depends on how fast the team can react to the damage, typically a few minutes or even no time at all. However, there is a limit to this recovery feature. It cannot recover a single account back to a previous point in time or recover just a particular chosen part of your data.
Therefore, Rewind is recommended in this situation as it gives you a micro-backup of your account only. Thanks to Rewind, your backup process becomes much more flexible. Rewind backs up every item in your web apps individually, enabling you to freely choose your way of restoring data. It is possible that you recover the entire account back to a previous point in time or just an item that was deleted, for example, a product.
You can not make sure that your account is perfectly safe from cyber attacks as there is always a possibility of human error, malicious attacks, and software glitches caused by 3rd party software. Thus, your web apps’ backups and recovery can be simple with an automated backup service like Rewind.
What is more impressive about Rewind is that it will not take a lot of your time. You just need an afternoon each week to manage your recovery or maybe your own IT team will help you to restore all types of possible data.
Tutorial for BigCommerce security
According to a report by Data Breach Investigations, there is a deep dive into trends in retail cyber attacks. These attacks target prominently at payment information, and even point-of-sale breaches and card skimmers are decreasing, e-commerce attacks still keep rising. We all know about the devastating result of losing customer data, it hits your brand reputation and may make you pay some associated fines. Hence, there are some practices that can help you secure your BigCommerce store.
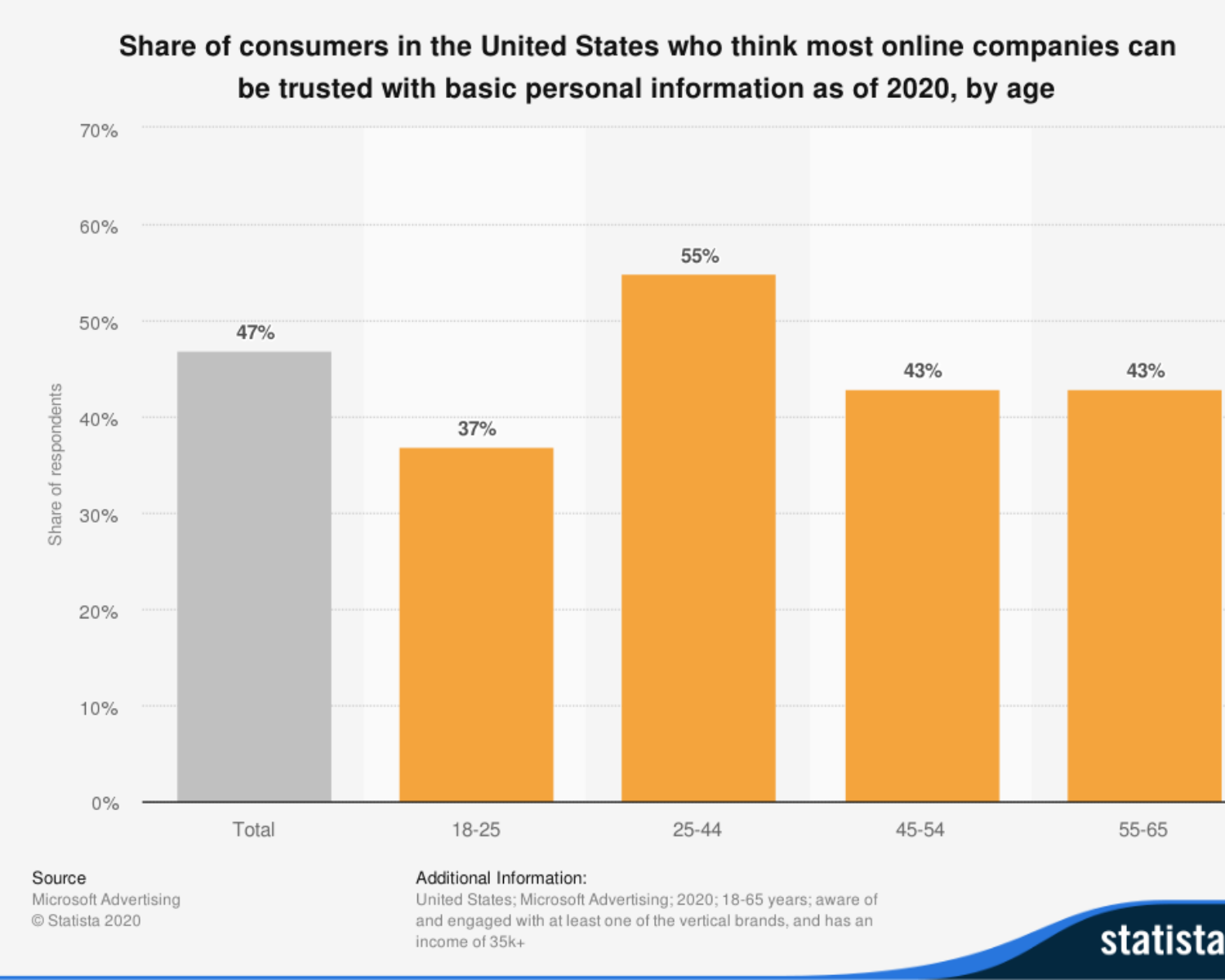
Create strong, unique passwords
It is estimated by the 2020 Verizon Data Breach Investigations Report that 37% of credential theft breaches used stolen or weak credentials. Thus, you should make an effort to protect your information and that of your shoppers as well. Make sure you, your employees, and your customers use a strong password to log in to the site.
- A strong password contains at least eight characters, upper and lowercase letters, numbers, and special symbols as well
- Passwords must be kept privately, each user should create his or her own strong username and password
- You should not use the passwords for an e-commerce site for any other sites
- Using a password manager should be considered
- You should not public your personal, sensitive information like date of birth, social security number, or any other info you may use as answers to security questions
Make sure your devices are safe
Whether you have got just one PC or laptop at home or an operation center of a full-linked computer, spend your time making sure that these devices are protected from cyber-attacks. In this case, anti-virus software, firewalls, or another appropriate method are likely to help your devices.
Steel against social engineering attempts
Malware is absolutely a great threat to your online stores. You can stay away from the phishing traps by avoiding malware infections, which is considered one of the best ways. Any level of your sensitive information must be kept securely until you have verified the receiver’s identity. In addition, you should keep in mind that no legitimate organization will ever require you to share your password.
Stay away from any links from suspicious emails as those links will lead you to a webpage that has been made to look like a familiar login page to steal your personal information. Moreover, you should stay conscious of the safety and originality of the attachments which you want to download.
I know attackers always make their attempts sophisticated, that’s why this article provides you with a few ways to distinguish phishing attempts from legitimate emails:
- A distrustful email can be indicated by evident spelling and grammatical mistakes in the subject line or its body
- Check the domain of the email’s sender carefully as it can be initially legitimate, but the spelling could be missing one letter with the purpose to trick your notice and make you click anyway to a risky domain. (e.g., BigCommerce.com could become BgCommerce.com)
- Do the same check with the URLs. As any URLs can contain phishing attempts, you should make sure the spelling is exact, with no missing letters. If you do not look closely, you may not notice the differences, which will take you to a dangerous domain.
- The most suspicious email is an email that requires you to provide your information, typically credit card, transfer money or authorize a charge. You might doubt it but those attackers will find an excuse why it must be done and sometimes is immediate.
BigCommerce apps for fraud prevention and security
BigCommerce always wants to provide online store owners and shoppers with the most secure experience on their platform. Hence, there are many BigCommerce apps for fraud prevention and security.
1. Brex

Brex is developed to make it easier for you to set up your complete business account, including credit cards, cash management, expenses, and accounting in just one place. Brex will take you only about 10 minutes to start an account, get an account number, routing number, and credit cards instantly upon approval, with no personal guarantee.
Moreover, there are many more features that you should take into consideration like uncapped rewards on all card spend, live support in minutes, or FDIC-insured, which keep your cash safe with FDIC insurance up to $250,000 offered through Brex Cash program banks.
2. Signifyd

When running your BigCommerce business, you may face a lot of challenges such as billions of dollars lost in chargebacks, customer dissatisfaction from mistaken declines, and operational costs due to tedious, manual transaction investigation. That is the reason why Signifyd was developed, it will help you solve all the problems above.
It is a full-service cloud platform that supports Signifyd’s guaranteed fraud protection. This platform deals with fraud prevention through real-time machine learning, enabling your business to expand scales and open new markets while reducing risk.
Signifyd will automatically check your shoppers’ order and tell you whether to ship it or not., which helps you concentrate on increasing sales with zero fraud liability.
3. Eye4Fraud

Eye4Fraud is one of the best ways for you to stay away from fraudulent transactions that cost you time, money, and annoyance. Eye4Fraud will seamlessly integrate with BigCommerce to provide you an outstanding fraud prevention service with the latest technologies and machine learning capabilities.
Eye4Fraud meticulously goes through all of your customers’ orders then finds fraudulent transactions. This process will both save your time and thousands of dollars in merchandise/shipping/returns costs every year. Besides, if installed on your BigCommerce store, Eye4Fraud also provides a chargeback guarantee: when there is an approval failure, they will solve your problems by guaranteeing the order and putting their problem-solving skills to the test.
4. Bolt Fraud Protection

Bolt Fraud Protection is an Elite Technology partner and preferred Fraud Vendor, which literally takes no time to integrate with BigCommerce but serves as an excellent fraud protector. Bolt Fraud Protection guarantees 100% chargeback and it also works with the standard BigCommerce checkout solution to detect fraud losses from your BigCommerce store.
Moreover, one more thing that makes Bolt remarkable is that it has proprietary behavioral data with 200+ real-time signals from the buyer’s shopping journey (about 4 times higher in contrast with its competitors), which enables Bolt to approve orders quickly. Bolt Fraud Protection’s experienced risk team is responsible for supporting this real-time approval by manually checking additional orders. Thanks to Bolt Fraud Protection, you are now able to fulfill more orders, increase sales without concerns about potential losses or liability.
5. ClearSale

When it comes to ClearSale, you should once go through their outstanding numbers: 19+ years in business, 99% client retention rate, more than 4000+ direct clients, accepting orders in over 160 countries every day. You may ask how, and below is the answer.
ClearSale was created to detect and eliminate fraud and chargebacks on your BigCommerce store. ClearSale has been making efforts to provide users with the highest approval rates and lowest false-positive rates in their business.
ClearSale carefully checks all the orders to give store owners the exact determination of fraud risk and then handles each transaction as necessary. With ClearSale, you will no longer have to worry about fraud, just concentrate on growing your business and opening new markets as well.
However, if you doubt ClearSale’s screening programs, you should know about their seasoned analyst responsible for approving orders. ClearSale is confident that their proprietary manual review process will never initially deny outright and make you happy to see higher approval rates while virtually eliminating false positives.
6. FraudLabs Pro

FraudLabs Pro is another fraud prevention and security app that you should take into consideration for your BigCommerce store. FraudLabs Pro will keep your business safe from malicious fraudsters by screening all order transactions. This app provides your online site with comprehensive and advanced algorithm engines that will approve such elements as geolocation, proxy, email, blacklist, credit card, transaction velocity, and others to find out fraud patterns. It will not interrupt your customers’ checkout process and also make detailed reports of all orders.
Moreover, FraudLabs Pro is well known for its impressive key features such as blacklist validation, export-controlled country validation, malware exploit validation, custom rules trigger, FraudLabs Pro Merchant Network, FraudLabs Pro Merchant Administrative Interface, email notification of fraud orders, mobile app notification of fraud orders and social profile query…With 10 years of experience FraudLabs Pro, all you need to do is to focus on your business and increase sales.
7. NoFraud

NoFraud is a fraud prevention module that uses real-time virtual identity verification. Their process includes fraud score analyzing, fraud rule building, and manual review, which helps them make individual, real-time decisions for each transaction using thousands of data points and every fraud detection technology available.
You do not need to worry about time for NoFraud as this app is fully managed by in-house experts and they are always willing to answer all the questions on a decision. Another NoFraud plus point is that it does not require your commitments, monthly minimums, or integration fees.
With NoFraud, your business will be protected from fraud as once you install it on your site, it will screen all customer’s transaction has been approved for validation. Especially for great risk transactions, NoFraud will manually review the orders, which increases the order acceptance rate to the highest in the industry.
Moreover, NoFraud is able to screen phone orders, cancel fraud orders before 3rd party order fulfillment companies process orders and let online store owners customize the review process, all make NoFraud a great fraud protection app to install.
8. Firewall
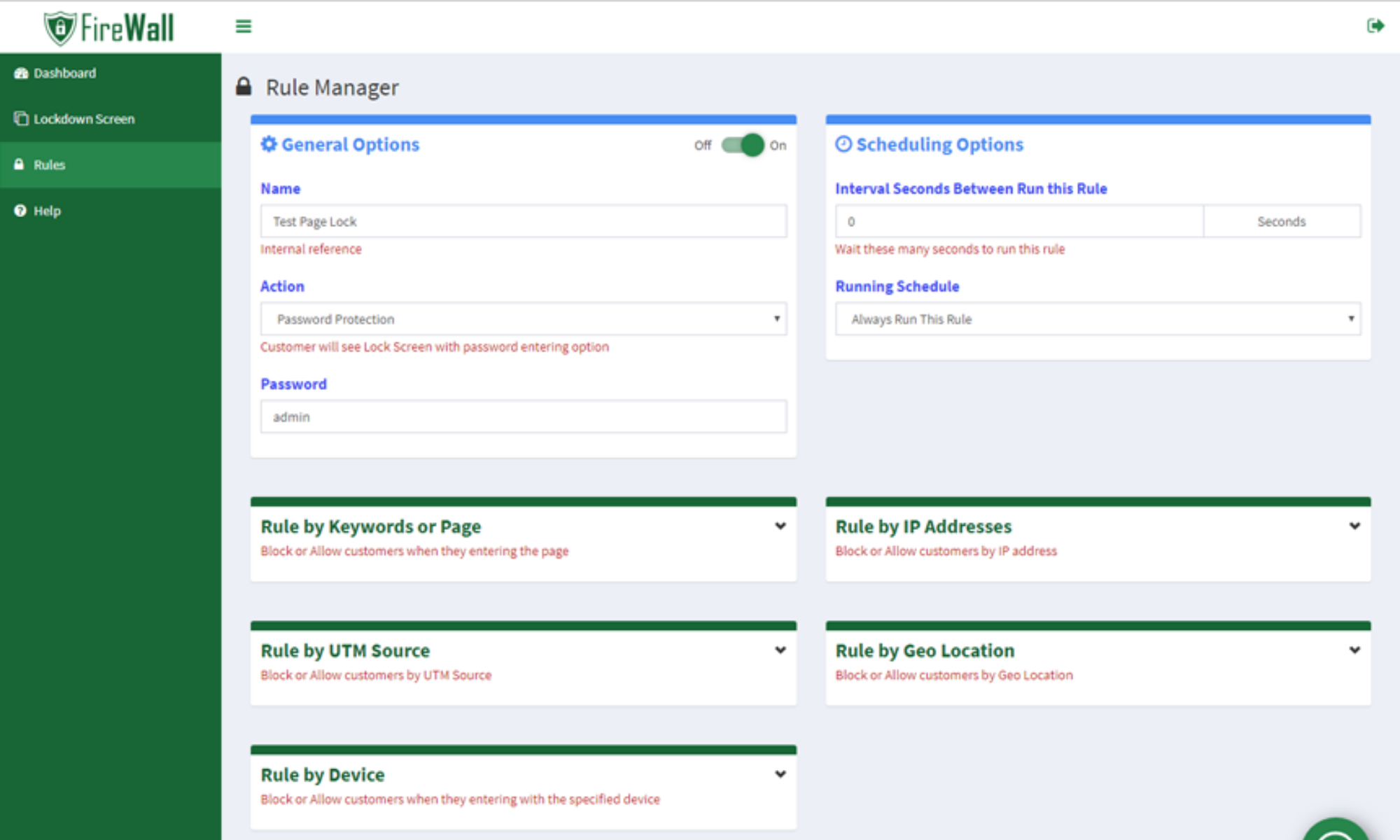
Firewall was developed to stop or redirect undesired countries, IP ranges, devices, or UTM sources. With the help of the Firewall app, mouse events like right-clicking on text, images, links, or input boxes and preventing drag & drop events, key pressing,..will also be knocked out.
In addition, Firewall will enable you to limit access to certain Products, Collections, Pages, Articles, Blogs; access based on customer location (GeoIP based locks); or block, unblock users by creating an IP range. With Firewall, some common features like “Copy”, “Cut”, “Paste” can be disabled to protect your site.
Conclusion
No matter how big or small your business is, it is possible that cyber attackers target your site. Hence, better e-commerce security practice is extremely important to the development of your business as customers’ data loss will not only cost you money but also will cause devastating damage to your store’s prestige.
A SaaS platform like BigCommerce can help you a lot, but there are still many more things to do. Do remember to create a strong password, be aware of clicking links and attachments from your mail. Additionally, review your third-party integrations regularly is also a useful tip to protect both you and your shoppers from threats.





